WikiLeaks publishes 'biggest ever leak of secret CIA documents'
The 8,761 documents published by WikiLeaks focus mainly on techniques for hacking and surveillance
The US intelligence agencies are facing fresh embarrassment after WikiLeakspublished what it described as the biggest ever leak of confidential documents from the CIA detailing the tools it uses to break into phones, communication apps and other electronic devices.
The thousands of leaked documents focus mainly on techniques for hacking and reveal how the CIA cooperated with British intelligence to engineer a way to compromise smart televisions and turn them into improvised surveillance devices.
The leak, named “Vault 7” by WikiLeaks, will once again raise questions about the inability of US spy agencies to protect secret documents in the digital age. It follows disclosures about Afghanistan and Iraq by army intelligence analyst Chelsea Manning in 2010 and about the National Security Agency and Britain’s GCHQ by Edward Snowden in 2013.
The new documents appear to be from the CIA’s 200-strong Center for Cyber Intelligence and show in detail how the agency’s digital specialists engage in hacking. Monday’s leak of about 9,000 secret files, which WikiLeaks said was only the first tranche of documents it had obtained, were all relatively recent, running from 2013 to 2016.
The revelations in the documents include:
The CIA declined to comment on the leak beyond the agency’s now-stock refusal to verify the content. “We do not comment on the authenticity or content of purported intelligence documents,” wrote CIA spokesperson Heather Fritz Horniak. But it is understood the documents are genuine and a hunt is under way for the leakers or hackers responsible for the leak.
WikiLeaks, in a statement, was vague about its source. “The archive appears to have been circulated among former US government hackers and contractors in an unauthorised manner, one of whom has provided WikiLeaks with portions of the archive,” the organisation said.
The leak feeds into the present feverish controversy in Washington over alleged links between Donald Trump’s team and Russia. US officials have claimed WikiLeaks acts as a conduit for Russian intelligence and Trump sided with the website during the White House election campaign, praising the organisation for publishing leaked Hillary Clinton emails.
Asked about Trump’s praise for WikiLeaks during last year’s election, when it published emails hacked from Clinton’s campaign chairman, Spicer told the Guardian: “The president said there’s a difference between Gmail accounts and classified information. The president made that distinction a couple of weeks ago.”
Julian Assange, the WikiLeaks editor-in-chief, said the disclosures were “exceptional from a political, legal and forensic perspective”. WikiLeaks has been criticised in the past for dumping documents on the internet unredacted and this time the names of officials and other information have been blacked out.
WikiLeaks shared the information in advance with Der Spiegel in Germany and La Repubblica in Italy.
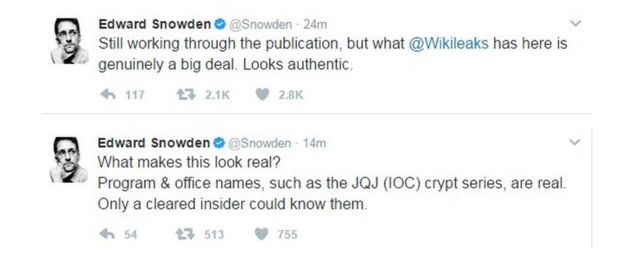
Edward Snowden, who is in exile in Russia, said in a series of tweets the documents seemed genuine and that only an insider could know this kind of detail. He tweeted:
The document dealing with Samsung televisions carries the CIA logo and is described as secret. It adds “USA/UK”. It says: “Accomplishments during joint workshop with MI5/BTSS (British Security Service) (week of June 16, 2014).”
It details how to fake it so that the television appears to be off but in reality can be used to monitor targets. It describes the television as being in “Fake Off” mode. Referring to UK involvement, it says: “Received sanitized source code from UK with comms and encryption removed.”
WikiLeaks, in a press release heralding the leak, said: “The attack against Samsung smart TVs was developed in cooperation with the United Kingdom’s MI5/BTSS. After infestation, Weeping Angel places the target TV in a ‘Fake Off’ mode, so that the owner falsely believes the TV is off when it is on. In ‘Fake Off’ mode the TV operates as a bug, recording conversations in the room and sending them over the internet to a covert CIA server.”
The role of MI5, the domestic intelligence service, is mainly to track terrorists and foreign intelligence agencies and monitoring along the lines revealed in the CIA documents would require a warrant.
The Snowden revelations created tension between the intelligence agencies and the major IT companies upset that the extent of their cooperation with the NSA had been exposed. But the companies were primarily angered over the revelation the agencies were privately working on ways to hack into their products. The CIA revelations risk renewing the friction with the private sector.
The initial reaction of members of the intelligence community was to question whether the latest revelations were in the public interest.
A source familiar with the CIA’s information security capabilities took issue with WikiLeaks’s comment that the leaker wanted “to initiate a public debate about cyberweapons”. But the source said this was akin to claiming to be worried about nuclear proliferation and then offering up the launch codes for just one country’s nuclear weapons at the moment when a war seemed most likely to begin.
Monday’s leaks also reveal that CIA hackers operating out of the Frankfurt consulate are given diplomatic (“black”) passports and US State Department cover. The documents include instructions for incoming CIA hackers that make Germany’s counter-intelligence efforts appear inconsequential.
The document reads:
“Breeze through German customs because you have your cover-for-action story down pat, and all they did was stamp your passport.
Your cover story (for this trip):
Q: Why are you here?
A: Supporting technical consultations at the consulate.”
The WikiLeaks press release said the leaks also reveal that:
• A number of the CIA’s electronic attack methods are designed for physical proximity. These attack methods are able to penetrate high-security networks that are disconnected from the internet, such as police record databases. In these cases, a CIA officer, agent or allied intelligence officer acting under instructions, physically infiltrates the targeted workplace. The attacker is provided with a USB stick containing malware developed for the CIA for this purpose, which is inserted into the targeted computer. The attacker then infects and extracts data.
• A CIA attack system called Fine Dining provides 24 decoy applications for CIA spies to use. To witnesses, the spy appears to be running a programme showing videos, presenting slides, playing a computer game, or even running a fake virus scanner. But while the decoy application is on the screen, the system is automatically infected and ransacked.
The documents also provide travel advice for hackers heading to Frankfurt: “Flying Lufthansa: Booze is free so enjoy (within reason).”
The rights group Privacy International, in a statement, said it had long warned about government hacking powers. “Insufficient security protections in the growing amount of devices connected to the internet or so-called ‘smart’ devices, such as Samsung smart TVs, only compound the problem, giving governments easier access to our private lives,” the group said.
• This article was amended on 22 March 2017 to clarify the attribution of parts of the description of the contents of the leaked material to the WikiLeaks press release.
7 March 2017
Wikileaks has published details of what it says are wide-ranging hacking tools used by the CIA.
The alleged cyber-weapons are said to include malware that targets Windows, Android, iOS, OSX and Linux computers as well as internet routers.
Some of the software is reported to have been developed in-house, but the UK's MI5 agency is said to have helped build a spyware attack for Samsung TVs.
A spokesman for the CIA would not confirm the details.
"We do not comment on the authenticity or content of purported intelligence documents," he said.
 TWITTER
TWITTERA spokesman for the UK Home Office was unable to comment.
Wikileaks said that its source had shared the details with it to prompt a debate into whether the CIA's hacking capabilities had exceeded its mandated powers.
Embarrassment factor - Analysis by BBC's security correspondent Gordon Corera
These latest leaks - which appear to give details of highly sensitive technical methods - will be a huge problem for the CIA.
There is the embarrassment factor - that an agency whose job is to steal other people's secrets has not been able to keep their own.
Then there will be the fear of a loss of intelligence coverage against their targets who may change their behaviour because they now know what the spies can do.
And then there will be the questions over whether the CIA's technical capabilities were too expansive and too secret.
Because many of the initial documents point to capabilities targeting consumer devices, the hardest questions may revolve around what is known as the "equities" problem.
This is when you find a vulnerability in a piece of technology how do you balance the benefit to the public of telling the manufacturer so they can close it and improve everyone's security with the benefit to the spy agency of leaving it in place so they can exploit it to collect intelligence.
The NSA has already faced questions about whether it has this balance right when many of its secrets were revealed by Edward Snowden, and now it may be the CIA's turn.
Hacked TVs
The effort to compromise Samsung's F8000 range of smart TVs was codenamed Weeping Angel, according to documents dated June 2014.
They describe the creation of a "fake-off" mode, designed to fool users into believing that their screens had been switched off.
Instead, the documents indicate, infected sets were made to covertly record audio, which would later be transferred over the internet to CIA computer servers once the TVs were fully switched back on, allowing their wi-fi links to re-establish.
Under a "future work" section, it is suggested that video snapshots might also be taken and the wi-fi limitation be overcome.
 SAMSUNG
SAMSUNGSamsung has not commented on the allegations.
Apple attacks
Wikileaks also claims that as of last year, the CIA has built up an arsenal of 24 Android "zero days" - the term given to previously unknown security flaws in code.
Some of these are said to have been discovered by the CIA, but others were allegedly obtained from the UK's GCHQ agency as well as the NSA and unnamed third-parties.
Devices made by Samsung, HTC and Sony, among others, were said to have been compromised as a result, allowing the CIA to read messages on Whatsapp, Signal, Telegram and Weibo among other chat services "before encryption is applied".

It is also claimed that a specialised CIA unit was set up to target iPhones and iPads, allowing the agency to see a target's location, activate their device's camera and microphone, and read text communications.
The unit is also reported to have made use of further iOS "zero days" obtained from GCHQ, the NSA and FBI.
"It is longstanding policy that we do not comment on intelligence matters," GCHQ told the BBC.
"Furthermore, all of GCHQ's work is carried out in accordance with a strict legal and policy framework, which ensures that our activities are authorised, necessary and proportionate."
Other claims say the CIA:
- was trying to find ways to infect vehicles' computer control systems. Wikileaks claims these might have been used for undetectable assassinations
- had found ways to infect "air-gapped" computers - machines that are not linked up to the internet or other insecure networks. Methods are said to have included hiding data in images or hidden parts of computer storage
- had developed attacks against popular anti-virus products
- had built up a library of hacking techniques "stolen" from malware developed in Russia and elsewhere
Wikileaks describes its release as the first in a series of planned leaks about the CIA's cyber-activities, which it refers to as Vault 7.
It added that the material had already circulated among hackers who used to work for the US government as well as contractors in an unauthorised manner.
Analysis: Mark Ward, Technology reporter
 REUTERS
REUTERSThere is a huge amount of information in the CIA data dump but a lot of it, such as its apparent success in compromising smart TVs, is not that surprising. Lone researchers have managed similar hacks, so smart government agents were always going to be able to go further.
Plus, we kind of know that a lot of the modern internet-of-things gear is broken as all kinds of holes have been found in all kinds of gadgets - including cars.
What's more interesting is the work said to have been done on iPhone and Android handsets. That's because Apple works hard to make sure iOS is secure and Google has made a real effort lately to secure its operating system. For a spy agency, access to those gadgets is key because they travel everywhere with a target.
What is likely to hit the CIA the hardest is losing control of all the zero day exploits and malware detailed in the papers.
It is more than likely that the agency paid millions to build up an arsenal of tools that are guaranteed to work - largely because they are based on flaws, bugs and vulnerabilities that have never been seen before. Operating systems of all stripes are really big haystacks and the information in some of the leaks looks like a good map to all the needles hiding within.
With the zero days now largely burned the CIA may have to re-trench for a while but it will doubtless have other unused attack tools stored and ready to deploy.
What's potentially more worrying is that as information about the bugs gets out then cybercriminals and other "bad guys" will pile in and use them.
We saw that with the zero days released in the much smaller Hacking Team data breach, and there is much more useful data to be found in this trove.
Ref:https://www.bbc.com/news/technology-39193008
asnthanhan blog's




No comments:
Post a Comment